Overview
Problem
Connecting to the public cloud IoT service requires the creation of credentials (e.g. private keys, certificates) per device. The provisioning and management of the life cycle of these credentials with the authentication and encryption of the device connections is a complex and human-intensive process that creates the following problems:
- Increases the setup cost and management especially for large scale deployments, for a process that needs to be repeated for each device
- Adds security risks related to the life cycle of the credentials.
Solution
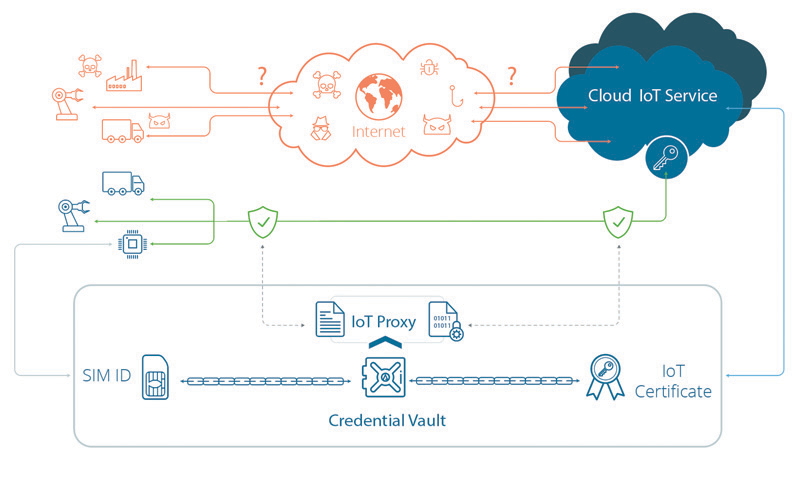
Cloud Services Connector is a secure cloud gateway for the devices running inside our private network that need to connect to IoT services in the public cloud.
It automates the identity, certificate creation, and management, linking the device/SIM identity with the unique cloud credentials and includes a proxy that will forward traffic from these devices to the public cloud IoT service of choice.
It supports AWS IoT Core and Azure IoT Hub cloud services.
Benefits
Thanks to the automated provisioning and secure proxy capability, the cloud connector brings these major benefits:
- Secure management of credentials and connectivity to public cloud services
- Reduce the cost of deployment and management through automation and zero-conf device provisioning
- Enable constrained devices to connect securely to the public cloud even if they cannot support encryption and certificates
- Remove risks of legacy/compromised ciphering protocols for long-lived devices
- Reduce cost by avoiding TLS traffic overhead on cellular metered bearers
- Everything as a service, without the need to manage infrastructure.
Use Cases
- Automated Provisioning
The Cloud Connector automates the provisioning of devices to public cloud IoT services, removing the need for manual steps on the device or cloud - Secure management of cloud credentials
The device identity is linked to the SIM, with unique credentials securely generated and stored, avoiding the risk and complexity of managing private keys, certificates and authentication. - Cloud migration
The Cloud Connector is network agnostic, allowing the migration to a different account or between different cloud IoT services - Connection to cloud from constrained devices
No deployment needed for devices. Devices with limited compute capacity and unable to manage certificates or encryption, can communicate with the Cloud Connector Endpoint inside a secure private network.
Capabilities
Cloud Services Connector has 2 main capabilities:
- Cloud Account Manager
- IoT Proxy
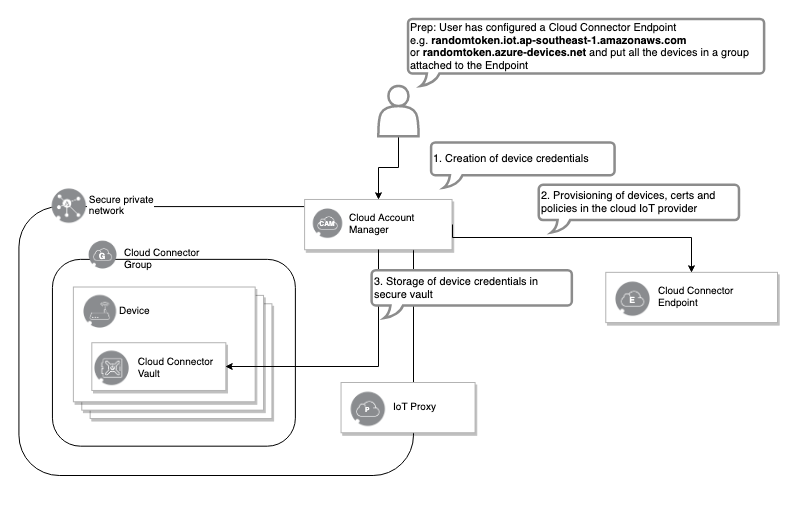
Cloud Account Manager
Automates the process for provisioning devices to public cloud IoT services, eliminating the need to create, download and manage unique credentials or any other custom configuration for each device through the following process:
- Generate each device required credentials.
- Provision the device with appropriate policies in the cloud IoT service on behalf of the customer.
- Store each device key in a dedicated private network vault as part of key management service, and chain it to the trusted SIM identity.
IoT Proxy
Once a device is provisioned for the Cloud Services Connector, it offers a proxy endpoint that will forward traffic from the private network to the public destination of choice (e.g. AWS IoT Core, Azure IoT Hub). The proxy endpoint is private, accessible only to IoT devices in the account.
The proxy performs different functions:
- A forward proxy function, accepting MQTT traffic over a secure private channel from the devices in a Group and forwarding it to the configured Endpoint
- Authenticates devices based on the SIM identity and adds the required encryption and authentication information to the cloud IoT service
- For Azure IoT Hub transforms the MQTT messages when needed, so that they are properly understood by the cloud IoT service. See more details here.
Resources
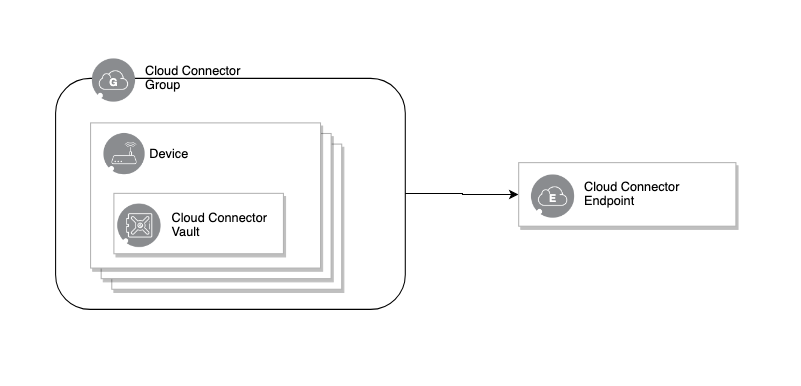
- Cloud Connector Endpoint
Used to model the destination for your MQTT IoT data.
An IoT service endpoint represents the public endpoint provided by your public cloud service provider.
There are 3 types of endpoints supported:- AWS IoT Core where the destination is the AWS IoT Core cloud service (e.g.
my-account.iot.xx-xxx-x.amazonaws.com) - Azure IoT Hub where the destination is the Azure IoT Hub cloud service (e.g.
my-iot-hub.azure-devices.net) - MQTT broker where the destination is any other MQTT message broker available on the internet (e.g.
mqtt.company.com)
- AWS IoT Core where the destination is the AWS IoT Core cloud service (e.g.
- Cloud Connector Groups
Used to group devices for connectivity to different endpoints, where a device may only exist in one group at a time.
Each Cloud Connector group can only have one configured Endpoint and can contain any number of devices.
AWS and Azure IOT services impose a service limit on concurrent connections and throughput, therefore we can only support up to these limits.
- Cloud Connector Vault
Each device grouped into a cloud connector is provided with its own secure vault for each of its identities and credentials. These secure vaults and identities are managed for you. The private keys cannot be recovered but can be deleted if needed.
Configuration and Limits
- Each Cloud Connector group can contain any number of devices.
AWS and Azure IoT services impose a service limit on concurrent connections and throughput, and can only support up to these limits. - Each Cloud Connector group can only have one configured Endpoint.
- Each device gets its own Vault.
- Cloud Account Management is only available based on the type of public cloud endpoint, AWS IoT or Azure IoT.
How it Works
The Cloud Services Connector securely links the devices SIM identity to the identity in the cloud, provisioning the devices and their identity in the cloud IoT services, forwarding the traffic from the devices to the appropriate cloud IoT Endpoint.
Cloud Account Manager
Automates the provisioning of devices to cloud IoT services. Provisioning is for the Endpoint that has been configured for the group of devices. Provisioning to the cloud IoT service is on behalf of the user and therefore requires IAM API keys. Cloud Account Manager is compatible with AWS IoT and Azure IoT Endpoint types.
Each device requires the following steps:
- User configuration of an Endpoint to AWS IoT Core of Azure IoT Hub and adds all devices in a Group to that Endpoint.
- Key creation and self-signed X.509 Certificate depending on the cloud IoT service:
- For AWS IoT Core the AWS IoT cert generation service is used
- For Azure IoT Hub the Cloud Service Connector generates the certificate.
In both cases, the certificate will be an RSA 2048 key.
- Device provisioning in the cloud IoT Service.
- For AWS it will create a Thing, Policy and Certificate and will attach the Certificate to the Thing and Policy.
- For Azure it will create a device and link it to the Certificate thumbprint.
If a certificate exists attached to the device this step will remove it and will use the new one. This is important if an old certificate has been compromised and/or needs to be rotated.
- Credentials (cert and private key) uploaded to the Cloud Connector Vault where they will be stored and encrypted with a unique vault password.
- Credentials attached to the device in the Cloud Services Connector which will link the credentials that have been created and provisioned in the cloud with the device’s SIM identity.
This process is repeated for each device in the Cloud Connector Group up to 15 devices per second since that’s the limit for the cloud providers.
These steps are automated, however, they can be run one by one for each device if there is a need for more control of each step. Be aware that this manual provisioning brings additional risks and responsibilities and for this reason, the automated provisioning is recommended.
After this process is finished all devices will be registered to the cloud IoT service and the Cloud Services Connector will be ready to accept connections and forward them to the corresponding cloud endpoint.
IoT Proxy
Once a device is provisioned, and connected to the private network it can then access the Cloud Connectors Service at:
- mqtt://mqtt.asavie.network:1883
- mqtts://mqtt.asavie.network:8883, with the DigiCert Global Root CA.
These endpoints and their IP 198.18.8.3 will never ever change and will remain configured in your IoT MQTT device applications.
The cloud connector service is only accessible by devices within your private network and not from the Internet. When you connect a device to a known service, its SIM identity automatically chains to the cloud service identity, solving IoT on-boarding problems through complete automation.
Once your devices are using the cloud connector service, all future configuration occurs via the cloud API.
Plain vs MQTT over TLS
Devices can send the traffic to the IoT Proxy using plain MQTT (port 1883) or in MQTT over TLS (port 8883).
Sending it in plain MQTT enables constrained devices that are not able to manage certificates or encryption to secure the connector to the cloud. If additional encryption is needed then TLS using server-side certificates can be used. This requires the device to store the server certificate chain for connection.
To send traffic over TLS the device will have to DigiCert Global Root CA. It can be downloaded in .pem format here
Forwarding Traffic
Once the Cloud Connector proxy is reached it will:
- Retrieve the credentials attached to that device from the vault.
- Apply TLS encryption and authenticate on behalf of the device using the device private key.
- Forward the traffic to the appropriate cloud IoT Endpoint.
Security
Best Practices
- Automated Provisioning:
- Once provisioning is completed by the Cloud Account Manager the user should delete/revoke cloud IAM API keys.
- Manual Provisioning (not using the Cloud Account Manager):
- User is responsible for creating strong keys and correct certificates for each cloud provider.
- Private keys are created in a local environment and then stored in the vault which brings additional security risks.
Users should delete the local copy of the private keys after they have been stored in the Cloud Connector Vault.
Other Security Considerations
- The IoT proxy will encrypt the traffic towards the cloud IoT services using TLS 1.2 always with the recommended cipher suites.
- The device credentials stored in the vault and used for the TLS encryption can be gathered only internally by the proxy application at runtime and removed from memory after every use. They cannot be retrieved through the API even with the vault password.
- For the automated provisioning
- The certificates generated are X.509 self-signed certificates in order to minimize the impact of any device credential being compromised.
- The policy used in AWS is:
`
{
“Version”: “2012-10-17”,
“Statement”: [{ "Effect": "Allow", "Action": "iot:*", "Resource": "*" }]
}
What’s Next?
The configuration and management of the Cloud Connector are available through APIs.
See the following guide for Automated Provisioning.